
Critical infrastructure and industrial facilities are well underway to harnessing Industry 4.0 connectivity and optimization. The systems at the heart of facilities, however, are prized targets for malicious actors. The equipment and processes relied on to maintain productivity of indispensable goods and services are frequently targeted due to the scope of impact a disruption can cause, as well as the numerous vulnerabilities inherent to the technology.
Facilities undertaking a digital transformation face security hurdles that bringing widely distributed legacy operational technology (OT) online entail. The productivity rewards from converging OT (including supervisory control and data acquisition (SCADA) and industrial control systems (ICS)) with IT are offset by the potentially catastrophic consequences a compromised system can create. Legacy OT designed to perform behind the safety of an airgap has a deployment lifetime of 10 to 20 years, is notoriously difficult to patch and can generate adverse kinetic responses when compromised. While infiltrated IT systems can lead to data leaks and service unavailability, unauthorized OT manipulation can result in human casualties, interruption of goods and services, property damage and environmental harm.
Powerful rugged edge computing introduced to the facility provides several key security features that can safeguard against physical and cyber attacks. Computers hardened to withstand the physical rigors of facility floors efficiently process workloads between legacy equipment, enterprise IT, industrial Internet of Things (IIoT) devices and newer cyber-physical systems. Moreover, many rugged edge computers are purpose-built to run protective applications from physically-secured hardware.
Trusted Platform Module (TPM)
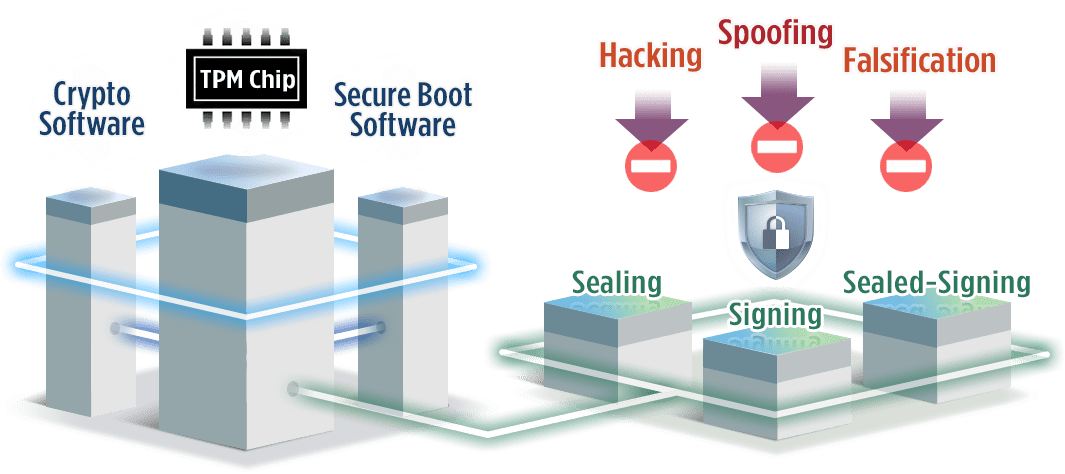
TPMs are secure cryptoprocessors installed by device manufacturers establishing a hardware-grounded root of trust. TPMs provide boot security for ICS, SCADA and other devices, ensuring that systems behave as intended. The modules eliminate openings for malware injections that can overtake systems and manipulate equipment, sensors and data feeds critical infrastructure and facilities rely on to safely and accurately uphold production and services.
The root keys secured within TPMs help authenticate devices on networks. Authentication helps form safe communications between rugged edge computers running operational applications and their connected equipment and sensors. Additionally, the root keys enable sound encryption for data and signals. Rugged edge devices intercept volumes of data normally processed in the cloud to deliver real-time processing on the manufacturing floor. By encrypting data in the environment, valuable system information is rendered indecipherable to unauthorized parties. Encrypted data can be safely stored on-site or transmitted to the cloud for backup storage.
Artificial Intelligence (AI)

Industrial GPU Computers processing seemingly-disparate data swarms through trained neural networks can conduct inference analyses detecting threats to facility systems. Parallel compute capabilities aggregate and process weather predictions, earthquake patterns and raw resource availability to anticipate threats to operations that have natural origins. Socio-political issues, economic irregularities and regional developments can be gleaned from dedicated databases, newsfeeds and social media to paint a picture of potential physical and cyberattacks, interruptions to supply and other scenarios that demand attention.
Industrial GPU computers deployed in the critical operating environment can also leverage AI to monitor network communications for malicious or errant code, or equipment performance for aberrant behavior. Trained AI systems can initiate protective and/or corrective measures to combat procedural irregularities, alerting system operators to situations requiring human intervention. Deep learning and machine learning models used hone AI systems to detect such issues quicker, more accurately and with less input as it accumulates data-processing experience.
Video Analytics

Rugged NVR computers employing a combination of CPU and GPU processors enable IoT surveillance systems in locations exposed to elements or other severe physical conditions. Decentralized surveillance can be established to cover outside perimeters for physical threats through video analytics applying license plate recognition, intrusion detection, facial recognition, behavior detection, object tracking and integrating with facility access control systems for a holistic, automated security platform. Inference analysis of visual data can easily discriminate true threat activity from movement of animals, foliage and weather manifestations.
Rugged NVR computers deployed on facility grounds can leverage GPU-powered AI toward complex computer vision algorithms, quickly identifying and responding to threats to workers, equipment and operations. Intelligent surveillance systems can quickly identify unauthorized personnel, unpermitted access to restricted or dangerous areas, unusual equipment activity and early, subtle signs that preventative maintenance could be in order. Thermal imaging analytics can bolster facial recognition applications through detection of deceptive facial prosthetics, as well as provide contactless initial screening for elevated body temperatures that could portend contagious disease. In addition to security implications, much of the visual data processed by rugged NVR computers can be applied toward process optimization and efficient resource allocation.
Premio Solutions

Premio offers a wide variety of rugged edge and industrial GPU compute solutions purpose-built to protect critical infrastructure and industry facilities from physical and cyber attacks. All Premio devices are secured with discrete modules upholding TPM 2.0 standards, protecting hardware and platforms on systems deployed in challenging environments.
Premio systems supporting robust CPU and GPU combination options deliver intelligent edge monitoring. Situational data processed through GPU-backed deep learning models provide inference analyses for actionable threat information with greater speed, sensitivity and accuracy than human monitoring can achieve.
Premio rugged edge computers are designed to meet a variety of durability standards for impact, vibration, electromagnetism and operating temperature. They feature numerous connectivity options to provide seamless communications to other networks, cloud resources and facility technology via 4G/LTE, Wi-Fi, Bluetooth and a variety of I/O ports. Promising robust, intelligent compute capabilities, Premio technology is designed to endure and secure critical infrastructure and industry environments.



