“The foundation of edge computing topology focus on specific models that balance workloads at the source of data: remote and mobile edge computing, IoT edge, and cloud edge are some great examples — It's pivotal to deploy edge hardware with built-in technologies for rugged, long-term reliability.”

What is a rugged edge computer?
Rugged edge computers are specifically developed to withstand the rigors of harsh usage conditions and are able to achieve a high level of durability through incorporating ruggedized features throughout its entire product design. From the external enclosure to the internal components, every piece of a rugged edge computer is purpose-built through a combination of mechanical and thermal engineering to address the issues of strong vibrations, extreme temperatures and wet or dusty situations.
Explore hardware solutions that address key fundamental features with Rugged Edge Computers

1. Wireless Connectivity
Access to Wifi, 4G LTE, Bluetooth and now 5G networks including GPS/GNSS location tracking allows more flexibility and possibilities for devices to gather important data points for new IoT technologies. In addition edge computers can process local data while transferring and offloading more compute intensive tasks to a cloud server thus increasing overall efficiency.
| Wireless Technology | Standard Supported |
|---|---|
| Wi-Fi 5 | EEE802.11ac/a/b/g/n |
| Wi-Fi 6 | IEEE802.11ax |
| 4G LTE | CAT 1-8 |
| 5G | Cat-M1; NB-IoT |
| Bluetooth | 4.x, 5.x |

2. Mobility and Remote Deployment
A key feature for rugged edge computers is the capability to be deployed in various mobile and remote locations decentralized from resources in the cloud. These types of applications often times have space fitting constraints and require compact form factors to fit into tight spaces. Therefore, a key foundation for mobility and remote deployments heavily rely on mission critical capabilities that ensure 24/7 reliability due to the lack of on-site technical support. The idea for mobility and machines actively running in remote locations leverage “watchdog” functions that allow for remote self-reset and system monitoring from a hub. Even operating software layers (Win 10 IoT) are designed to support edge and IoT functions with long-term service channel options, which basically avoid updates that can cause interruptions and detrimental downtime.
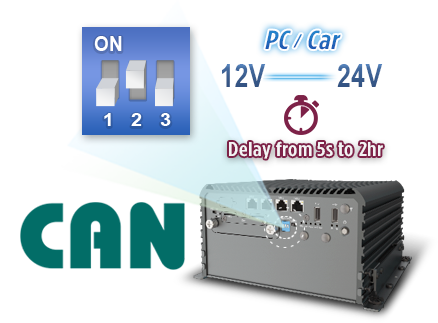
One example of edge computing is for in-vehicle environments, expanding the reach of computing power where current integrations are less capable or more decentralized. Access to CAN bus protocol enables predictive maintenance, one of the most sought after applications for railway, fleet managers, heavy machinery operators and first response vehicles. With deeper and real-time insights to vehicle's engine conditions, businesses can greatly reduce costs and downtime through scheduling repairs based on accurate data. Another in-vehicle feature that is best for rugged edge computers is power-ignition management; once toggled in car mode versus pc mode, this allows the computer to communicate directly with the car’s ignition and controls the on/off delay to ensure applications are not interrupted during the ignition process. Learn more about power ignition management.

3. Performance Accelerators
Gone are the days of simplistic edge devices that merely handed off data information from IoT sensors and actuators to the next stage for actual computing. Increase in processor performance, GPU or VPU based inference analysis, and large capacity data drives have empowered rugged edge computers to manage local analytics without having to move data over the network to the cloud thus saving bandwidth and eliminating latency effects. Additionally, high-speed NVMe solid state drives (SSD) rapidly feed awaiting CPUs, GPUs and/or VPUs swarms of data, eliminating bottlenecks between the processors and storage technology. These open the realm of real-time computing and better application performance. Autonomous robots can locally process camera information and immediately act upon the task at hand such as stopping its operation when something is blocking its way. Having to send camera information over a network for processing not only risks slow reaction times but runs into the issue of rising bandwidth costs and unstable connections.


4. Variety of I/O Ports and PCIe/PCI Expansion Slots
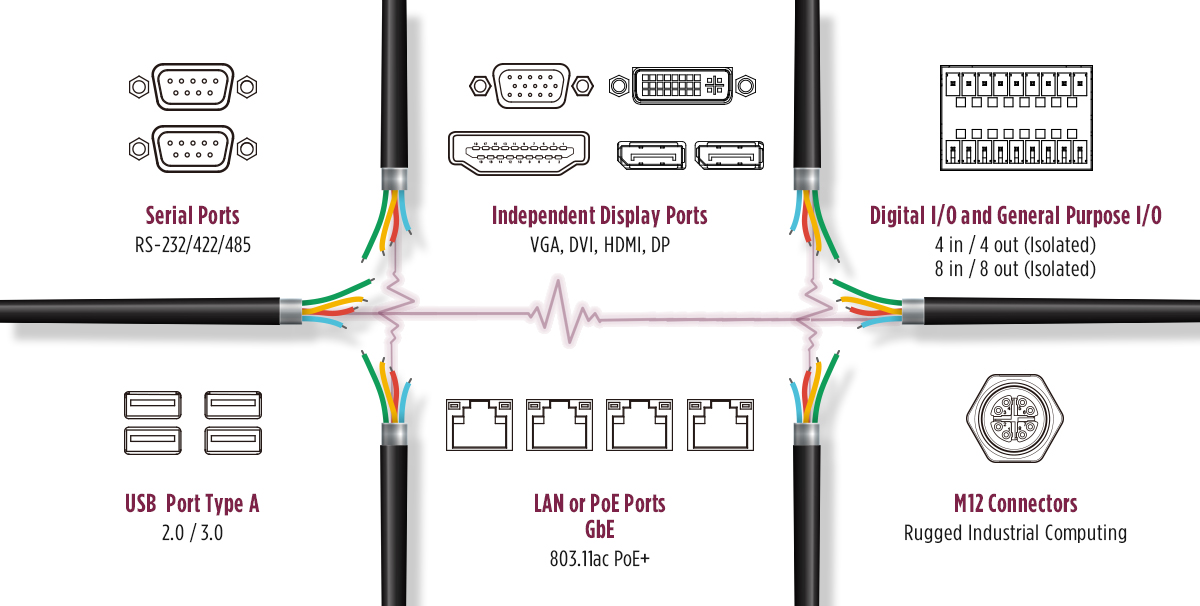
What allows edge computers to work so well is the capability to connect to various legacy and modern devices for data gathering both in legacy analog and digital IoT signals. By including GPIO and Digital I/Os, edge computers can capture signals from sensors of all kinds for actionable results. The ability to support multiple Universal Serial Buses (USB 2.0 and 3.0) are also key in today’s digital data transformation framework due to these sensors and devices leveraging high-speed and superspeed transfer rates up to 10 Gbps.
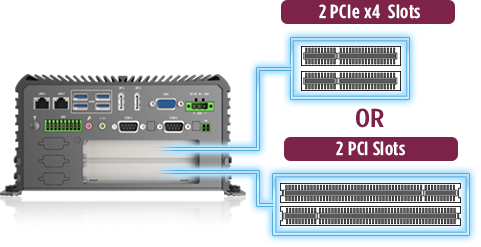
- Another critical feature is to have flexibility for application specific performance add-in cards through common computing standards like legacy PCI or current PCIe Gen 2,3 and now recently 4. This flexibility provides not only fast data transmission speeds but options for applications specific performance cards like GPU, VPU, or capture cards that communicate through the PCIe bus protocol.


5. Ruggedness and Security
Without proper protections against external environmental elements and factors that are harmful to sensitive computer components then edge computing won't be able to provide the benefits of real-time analytics in harsh operating environments. As a foundation for edge computing, features should include fanless designs, wide operating temperatures, varied voltage input ranges and high shock and vibration reliability.

In addition, at the core of edge computing it's imperative that deployment models ensure strengthened security, accelerated performance, and increased scalability. Security layers are equally important on both hardware and software layers, each working together to provide authentications for critical operations in mobile and remote locations. For example the Trusted Computing Group publishes the Trusted Platform Module (TPM 2.0) hardware specification that is an international standard adhering to modern security and privacy protection features.
According to Trusted Computing Groups press release, “[TPM 2.0] implementation in computing devices safeguards cryptographic keys; prevents private keys from being exported; shields PIN values used for authentication; and records and anonymously reports on software loaded during the boot process to protect against malware and attacks. As such, it will become an essential component of any comprehensive security strategy”… “The specification was developed as a set of commands that enable the TPM to be used in a variety of systems and devices, from PCs, servers and networking gear to embedded systems and the Internet of Things."

Industry 4.0 and IoT markets looking to integrate better data management will require rugged edge computers to unleash the next wave of innovation and growth. In addition to rugged environmental safety is the need for better security measures against potential risks and attacks. Edge computers configured as a nearby security agent for new walls of defenses in between IoT devices and outside connections. A well though out approach to edge computing will always accelerate performance, scale rapidly, and strengthen security in edge deployments with hardware and software layers.



