IoT Security at the Rugged Edge
The convergence of IT with vulnerable OT has exposed the inherent weaknesses that can result in attacks on the industrial IoT. Such vulnerabilities include poorly-secured industrial systems. AI/ML provides hyperintelligent cybersecurity and threat mitigation for platforms based on Industry 4.0. To date, the compute systems optimized to deploy responsive, powerful AI/ML are unsuited for the physical factors of heavy industrial settings. Rugged edge computers are purpose-built to reliably deliver intelligence in these challenging environments.
Join us at the IoT Device Security Conference hosted by Embedded Computing Design. Premio's Director of Technical Operations Robert Lu will address these issues, as well as the advanced compute, storage, connectivity, and ruggedized features that support reflexive, real-time AI close to the data sources. Tune in to get all the secret recipe behind successful deployments of IoT edge devices in challenging environments!
Here is the webinar recording from the virtual event in case you missed all the details. Robert Lu, Director of Technical Operations for Premio provides some insight into the importance of hardware security encryptions at the rugged edge with TPM 2.0
Trusted Platform Module (TPM) 2.0: Securing IoT Applications at the Rugged Edge
Compute system vulnerabilities pose significant risks to enterprises as sensitive data processing units become a potential target for cyberattacks once they are connected to the IoT. Therefore, hardware computers require a security armor - TPM 2.0 - to protect embedded compute systems.
TPM technology secures connected systems at the hardware level. Premio’s embedded and rugged edge computers are deployable with TPM microcontrollers protecting systems and data. This enterprise-level security is extended to IoT devices connected to systems through authentication and key management. Learn more about TPM 2.0.
Edge Computing at the Rugged Edge
Access and Storage in Cloud Computing
Cloud storage is one of the greatest benefits cloud comp uting has to offer. Any relevant business data can be stored in the cloud, which makes it more accessible and usable.
uting has to offer. Any relevant business data can be stored in the cloud, which makes it more accessible and usable.
Artificial Intelligence & Machine Learning
Artificial intelligence (AI) is the basis for mimicking human intelligence processes through the creation and application of algorithms that are built into a dynamic computing environment.
5G & Wireless Edge Network
5G wireless technology is meant to deliver higher multi-Gbps peak data speeds, ultra-low latency, more reliability, massive network capacity, increased availability, and a more uniform user experience for more users.
IoT And The Intelligent Edge
The Internet of things or “IoT” has rapidly led a digital transformation data-driven assets in multiple industries like manufacturing, transportation, and public utilities.
Transformative Driving Factors in Edge Computing
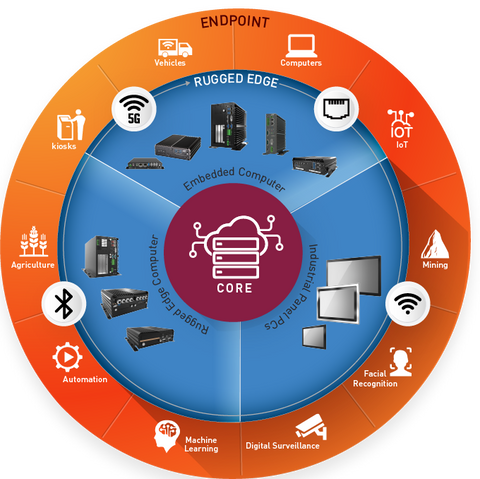
- Ultra-low Latency: We can no longer rely on the cloud due to high latency issues. Therefore, edge computing is needed to enable real-time decision making.
- Increased Bandwidth: Edge computing grants a greater bandwidth pipeline processing data locally. Network leveraging 10GbE transmit Ethernet frames at 10 gigabits per second, allowing edge devices to meet performance requirements for IoT applications.
- Security: Hardware compute systems require data protection by integrating TPM 2.0.
- Wireless Connectivity: Access to broadband options such as Wi-Fi 6 and 5G allows more flexibility and possibilities for devices to gather critical data points for new IoT technologies.
Three Driving Business Benefits (Hybrid Model of Edge and Cloud)
- Ubiquitous Intelligence (IoT + Cloud + AI) – Modeling training and inferencing workloads disaggregated and distribute across new AI applications.
- Edge Cloud Computing (5G + Cloud) – Base stations and cloud nodes communicating with endpoints for data but also still in proximity for necessary compute power and ultra-reliable latency. Balance workload dedicated to the applications.
- Autonomous Infrastructure (5G +AI) – Autonomy is a means to scale economically and operationally. Fully intelligent automation.





